Table of Contents
Authentication
Principles
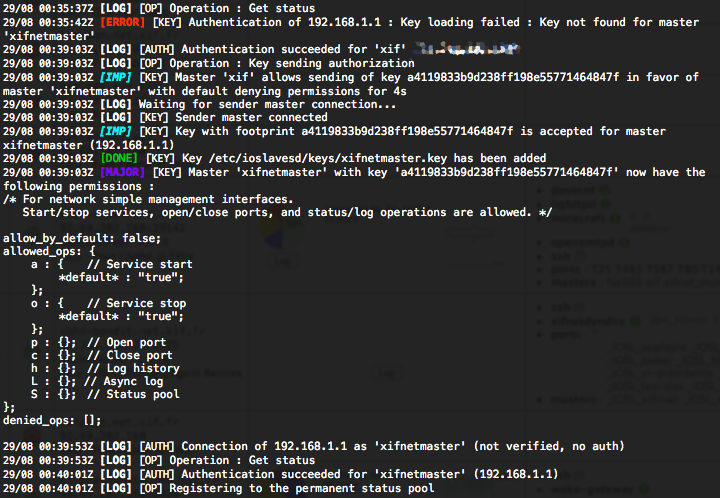
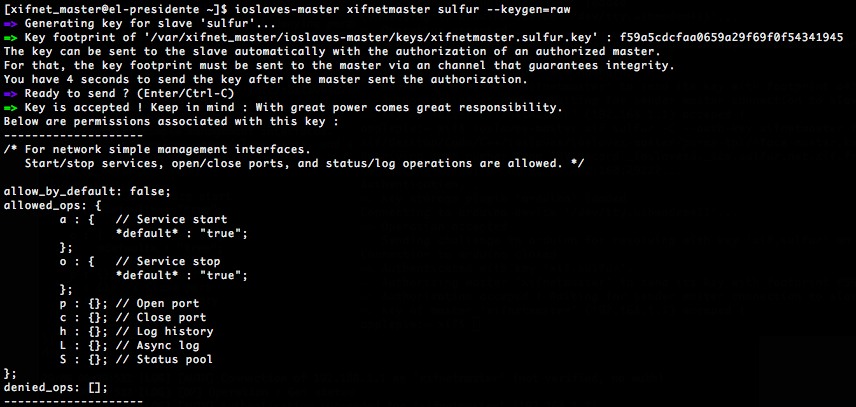
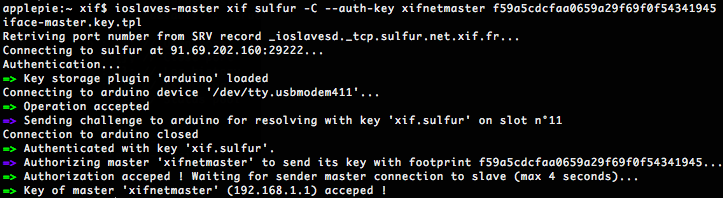
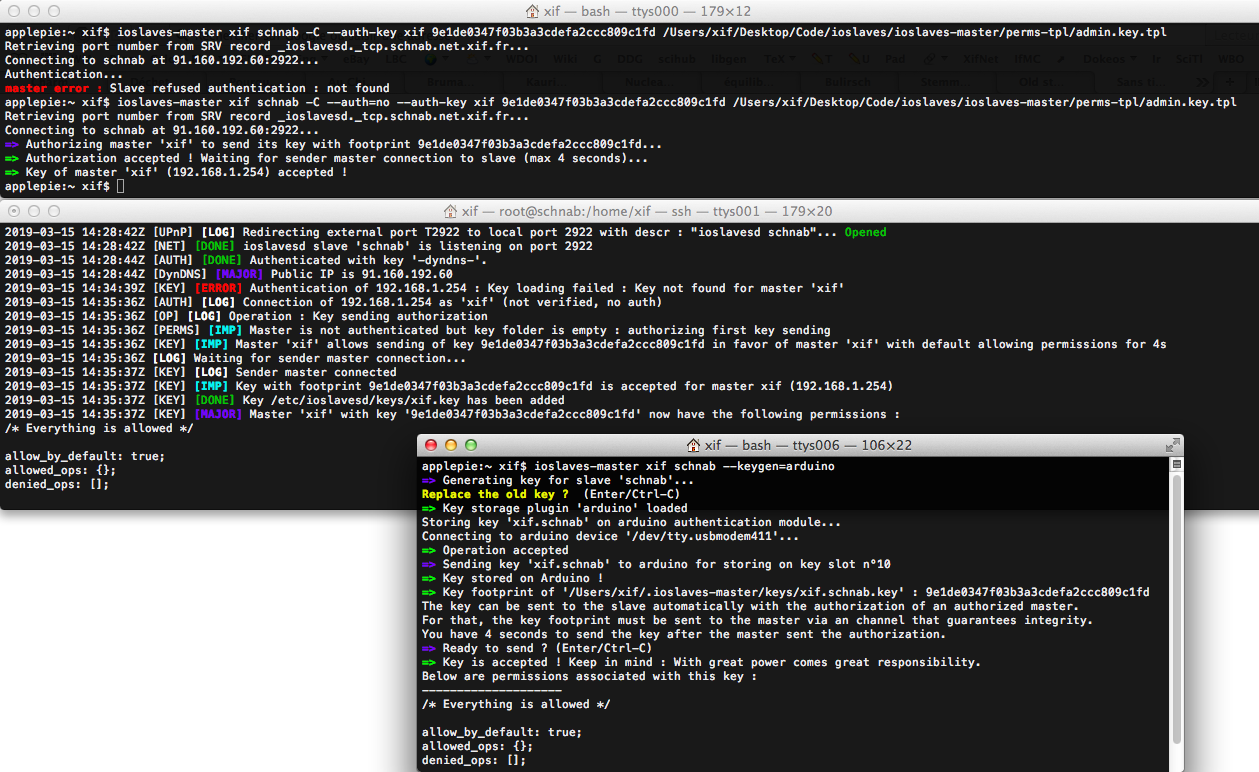
Just a hash challenge (actually using Whirlpool) to resolve for masters in order to authenticate themselves, using a symmetric key, that needs to be sent to slaves.
Key storage/auth methods
Plugins on master side can be made to store and do the hash in an other way than plain raw key storage on the master's filesystem.